911:Secret services
Site menu:
- Occult symbolism Intro
- History of oppression
- Social terrorism
- Economic terrorism
Intro
- Spies are despicable The Holy Bible Says That Spies Are Despicable!!
History
- Quote from Ignatius, Spying and Sedition-From A Work in Progress
- Prior to his journey across the English Channel, on his first begging journey to Bruges and Antwerp, Loyola encountered a Spaniard of high repute and learning. “He met at Bruges the Spanish humanist Juan Luis Vives, who had recently returned from his post in England.” (The Society of Jesus in Ireland, Scotland and England 1541-1588 by Thomas M. McCoog. Page 12, published by Brill, 1996.) Vives was a professor at the Louvain who had come to England at the invitation of Henry, acted as tutor to Princess Mary (later “Bloody Mary”), but was forced to leave England because he had declared himself against the divorce of Catherine of Aragon. (Encyclopedia Britannica,11th Edition, Handy Edition, 1911, Vol. 28, Pages 152-153.) This Spanish Papist was a connection for Ignatius to the Spaniards in England. He was an excellent Catholic role model for Ignatius, having produced a most bigoted and fanatic, religious murderess in his education of Mary. His up to date knowledge of England, together with letters of introduction from him would have provided open doors for Loyola throughout all strata of Catholic and Spanish society in England. Ignatius also would have been easily able to serve as a courier, bringing messages in and then gathering information for his Lord, the Pope. The beginning of Jesuit espionage and counterintelligence began with the founder of the Order, a calculating militarist who well understood the importance of reconnaissance, logistics and planning.... The early training of Loyola would later bear fruit in the spiritual surveillance, physical espionage, and a “human resource” inventory system that was developed within the Society. “The detective system which prevails to so iniquitous an extent amongst the Jesuits must prevent friendship by destroying mutual confidence"... Full dictatorial surveillance based on the Jesuit model was openly implemented in Western Europe under the Gestapo, and this was improved and expanded upon to control and permeate the intelligence agencies of all nations. It has birthed as well a fraternity of men who have demonstrated the ability to amass the wealth of the nations in heaps and piles across the globe for use to achieve the designs for world domination.
- Quote from Eric Jon Phelps on the Middle East:
- "Before commencing the body of this text, the author recommends the reading of his book, "Vatican Assassins: Wounded In The House Of My Friends”. Therein, the reader will be informed, fact-by-fact, as to the origin and perfection of the Jesuit Superior General’s International Intelligence Community. That Community is overseen by the Pope’s Sovereign Military Order of Malta headquartered in Rome and directed by its Grand Master, Andrew Bertie. Thus, the Jesuit General, also known as the Black Pope, controls the entirety of the American Intelligence Community, including but not limited to, the Federal Bureau of Investigation, the Central Intelligence Agency, the National Security Agency, the Defense Intelligence Agency, the Office of Naval Intelligence as well as the intelligence arms of the Army and the Air Force."
- This "Unified International Intelligence Community" was built during Rome’s Second Thirty Years’ War (1914-1945) and perfected during Rome’s subsequent Cold War (1945-1990).
- See also: UK–USA Security Agreement (1941)
- video: CIA Coup in Guatemala 1954 “A Coup Made in America”
- In Part 3: ‘The Catholic Church, the Guatemalan Military, and the Duck Test’:
- “The CIA contacts Cardinal Spellman in NY, to take part in their psychological war against Arbenz…. “ @ 4:19
- “We [the CIA] got the ‘okay’ from Cardinal Spellman to go ahead with this…”
- @ 5:33 CIA vet Howard E. Hunt states “We always said in an admiring way, that the Jesuits have formed the greatest intelligence service in the world, always have.”
- In Part 3: ‘The Catholic Church, the Guatemalan Military, and the Duck Test’:
- Quote from: Dave Hunt
"Leading Surveillance Societies in 2006" (from Daily Telegraph)
All serving the jesuits cia creating the internet cartel monopoly, and the greatest inteligence gattering tool ever known. [1]
- Secret Service & the Occult
- "It is not really surprising that historically occultism and espionage have often been strange bedfellows. The black art of espionage is about obtaining secret information and witches, psychics and astrologers have always claimed to be able to predict the future and know about things hidden from ordinary people. Gathering intelligence is carried out under a cloak of secrecy and occultists are adept at keeping their activities concealed from sight. Like secret agents they also use codes, symbols and cryptograms to hide information from outsiders. Occultists and intelligence officers are similar in many ways, as both inhabit a shadowy underworld of secrets, deception and disinformation. It is therefore not unusual that often these two professions have shared the same members."
Networks
International surveillance companies are based in the more technologically sophisticated countries, and they sell their technology on to every country of the world. This industry is, in practice, unregulated. Intelligence agencies, military forces and police authorities are able to silently, and on mass, and secretly intercept calls and take over computers without the help or knowledge of the telecommunication providers. Users’ physical location can be tracked if they are carrying a mobile phone, even if it is only on stand by.
- When citizens overthrew the dictatorships in Egypt and Libya this year, they uncovered listening rooms where devices from Gamma corporation of the UK, Amesys of France, VASTech of South Africa and ZTE Corp of China monitored their every move online and on the phone.
But the WikiLeaks Spy Files are more than just about ’good Western countries’ exporting to ’bad developing world countries’. Western companies are also selling a vast range of mass surveillance equipment to Western intelligence agencies. In traditional spy stories, intelligence agencies like MI5 bug the phone of one or two people of interest. In the last ten years systems for indiscriminate, mass surveillance have become the norm. Intelligence companies such as VASTech secretly sell equipment to permanently record the phone calls of entire nations. Others record the location of every mobile phone in a city, down to 50 meters. Systems to infect every Facebook user, or smart-phone owner of an entire population group are on the intelligence market.
Surveillance companies like SS8 in the U.S., Hacking Team in Italy and Vupen in France manufacture viruses (Trojans) that hijack individual computers and phones (including iPhones, Blackberries and Androids), take over the device, record its every use, movement, and even the sights and sounds of the room it is in. Other companies like Phoenexia in the Czech Republic collaborate with the military to create speech analysis tools. They identify individuals by gender, age and stress levels and track them based on ‘voiceprints’. Blue Coat in the U.S. and Ipoque in Germany sell tools to governments in countries like China and Iran to prevent dissidents from organizing online.
Trovicor, previously a subsidiary of Nokia Siemens Networks, supplied the Bahraini government with interception technologies that tracked human rights activist Abdul Ghani Al Khanjar. He was shown details of personal mobile phone conversations from before he was interrogated and beaten in the winter of 2010-2011. [7]
- See also:
- Todo: secret/military network infrastructures, financial payment infrastructures, encrypted lines.
Personal records
- Report on the Surveillance Society For the Information Commissioner by the Surveillance Studies Network[8]
- State number ("social 'security' number")
- Social profile
- Address
- Family composition (present and past genealogy)
- Health record
- Occupational record
- Educational record
- Legal record (police/court/fines/crime/jail)
- Political afiliations
- Financal record
- Bank accounts
- Income
- Taxation (private and corporate)
- Spending record (house loan, debt, consumer spending, investments, ...)
- Pension funds
- Social welfare record
- Travel record (visa's / state-entry, boarding logs: bus/metro/train/ferry/airline)
- Internet tracks (email, web sites & searches, ...)
- Personal character record (emotional/intellectual classification, pastime passions, luxury goods / entertainment spending, sexuality, etc.)
- Biometrics:
- Facial scans
- Fingerprints
- Eye scan
- Voice signature
- DNA signature
Special networks
ECHELON
- An international espionage network
Satellites
- Todo: Satellite operators, military networks, etc.
- Category:Communications satellite operators
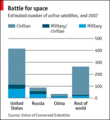
Estimate of the number of active satellites in space (source: Union of Concerned Scientists).
See also: US Space Surveillance Network, "Disharmony in the spheres"
DNA surveys from space
- Whistleblowing scientist Leuren Moret reveals Googles shocking ongoing plans and technology
- DNA surveys from space
- Biopiracy Takeover Scientist Leuren Moret blows the whistle on DNA surveys from space
- Google accused of biopiracy
Drones
- AeroVironment's Nano Hummingbird - Outdoor Indoor Flight
- View from the World’s Most Advanced Surveillance Drone
- Drones over US to get weaponized – so far, non-lethally
- An unclassified US air force document reported by CBS (pdf) news expands on this unprecedented and unconstitutional step – one that formally brings the military into the role of controlling domestic populations on US soil, which is the bright line that separates a democracy from a military oligarchy. (The US constitution allows for the deployment of National Guard units by governors, who are answerable to the people; but this system is intended, as is posse comitatus, to prevent the military from taking action aimed at US citizens domestically.) [9]
Phone tracing
- Todo:
- Mobile phone tracing/triangulation/wiretapping (passive/activated-by-defined-signatures and active/on-demand), identification.
- Mobile phone infrastructure (connection logs, voice/web data)
- VOIP provider data hooks/requests for secret services (Skype, Google Voice, etc.)
- Geotagging
- Are all telephone calls recorded and accessible to the US government?: A former FBI counterterrorism agent claims on CNN that this is the case
Internet
- Todo:
- ISP data-retention/IP-request laws and its enforcement
- Secret services and ISP collaborations
- Credit card purchasing information (privacy, fraud, etc.)
- Web browser cookie issues
- Email taffic espionage (gmail, hotmail)
- Search engine espionage (google)
- Software install espionage (anti-virus software, ...)
- Hardware/appliance espionage (ISP modems, consumer routers/switches, google appliance, ...)
- Jesuit Google and Facebook: Part of Rome’s International Intelligence Community
- Google to enlist NSA to help it ward off cyberattacks
- Intellipedia
- "Google has lots to do with intelligence" (March 30, 2008):
- "The system is modeled after Wikipedia, the public online, group-edited encyclopedia. However, the cloak-and-dagger version is maintained by the director of national intelligence and is accessible only to the CIA, FBI, National Security Agency and an alphabet soup of other intelligence agencies and offices. Agents can log in, depending on their clearance, to Intellipedia's three tiers of service: top secret, secret and sensitive but unclassified. So far, 37,000 users have established accounts on the network, which contain 35,000 articles encompassing 200,000 pages, according to Dennehy. Google supplies the computer servers that support the network, as well as the search software that allows users to sift through messages and data."
- "Google has lots to do with intelligence" (March 30, 2008):
- AxisGlobe eastern secret service news.
- Facebook Google are cia fronts
Social networking
- Social Networking Sites and the Surveillance Society
- Pentagon sets its sights on social networking websites
- Revealed: US spy operation that manipulates social media
- Corporate manipulation of social media: Example: Monsanto on Reddit
- Profiling/Searching populations through Facebook, MySpace (owned by Rupert Murdoch)
Security/privacies issues
- Information gleaned from social networks has cost people jobs, led to suspensions and expulsions, damaged prospects for employment and university admission, helped crooks defraud victims and generated criminal charges. Universities scour social networking sites for evidence of residence keg parties, in violation of campus policies. Admissions officers use them to evaluate university-bound students. Police tap into them to investigate underage drinking and sexual activity. Companies check out Facebook to help with direct marketing campaigns. And increasingly, employers are using them to screen prospective employees....“Anything on the site, Facebook can see and data mine,”
- For companies that engage in Datamining “Not only is it a wide range of personal information that’s cross-referenced and verified by the individuals themselves, but people themselves are volunteering this information.”
- Risks associated with the use of social networks
- Data, once published, may remain there forever;
- Traffic data may be shared with third parties, including advertisers and law enforcement agencies;
- Third parties may misuse the data they obtain;
- Photos posted to social networking sites may be connected to facial recognition software and become universal biometric identifiers
- The availability of personal data in user profiles could lead to increased identity theft.
- video: Does what happens in the Facebook stay in the Facebook?
- video: Major Facebook security hole lets you view your friends’ live chats
- video: Julian Assange: Facebook "Most Appalling Spying Machine Ever Invented"
- Identity 'at risk' on Facebook
- Facebook's New Terms Of Service: "We Can Do Anything We Want With Your Content. Forever."
- Quebec police arrest teen for allegedly promoting ethnic hatred on Facebook
- Facebook tracks your every move, even after logging out (online)
- "Even if you are logged out, Facebook still knows and can track every page you visit," Cubrilovic wrote on a recent blog posting. "The only solution is to delete every Facebook cookie in your browser, or to use a separate browser for Facebook interactions" (http://nikcub-static.appspot.com/lo...). But how many Facebook users will actually know to do this? The site has never announced to its users that it is even tracking them in the first place, let alone given them any instructions on how to "opt-out" of this egregious invasion of privacy. Facebook, of course, has become infamous for simply changing its site setup, including privacy settings, and leaving it up to users to figure out how to contain their breached information after the fact. It has switched from an "opt-in" approach, where users used to be given the option to "upgrade" to new features, to a much more complicated "opt-out" approach, where Facebook makes drastic changes and leaves it up to users to somehow figure out how to change things back to the way they were (if such an option is even still possible).
- Facebook Privacy Nightmare: How the site tracks you, even when you're offline
- Facebook Monitors Your Chats for Criminal Activity
- Facebook's Privacy Issues Are Even Deeper Than We Knew
- Questions about what social networks mean for personal privacy and security have been brought to a head by research at Carnegie Mellon University that shows that Facebook has essentially become a worldwide photo identification database. Paired with related research, we're looking at the prospect where good, bad and ugly actors will be able identify a face in a crowd and know sensitive personal information about that person.
- German officials reopen inquiry into Facebook facial recognition
- Big Brother is Not Only Watching You: He is Your Facebook Friend
- Facebook new cointelpro what do you mean by no snitching?
- I do not think the old way of U.S. Government spying and surveillance has become obsolete, but with the invention of Facebook, it has provided law enforcement with a wealth of information on the identity of people, the various alias they use, photos of family and friends, what city and state they live in, etc., and not to mention the incriminating chat that takes place on Facebook. Facebook is the new FBI dossier and it doesn’t require the manpower or the man hours, nor will it be met with the same public resistance of Cointelpro of the past. They have done a superb job of luring people to sleep with the whole concept of social networking and have relaxed the Sheeple so much that they are enjoying and having fun in their own demise. This doesn’t require coercion or interrogation (that was once associated with KGB, Mossad, CIA, etc.) and a covert government plot to accumulate or access intimate files on American citizens in particular and citizens throughout the world in general (not to suggest that the old mode of acquiring intelligence has outlived its usefulness). The people have become so dumb down that they are voluntarily providing law enforcement with massive data under the guise of social networking. ]
- Facebook's Graph Search: Kiss Your Privacy Goodbye - see Facebook's Graph Search
- Similar check Wolfram facebook report
Spyware
- FinFisher
- Google security engineer Morgan Marquis-Boire and Berkeley student Bill Marczak were investigating spyware found in email attachments to several Bahraini activists. In their analysis they identified the spyware infecting not only PCs but a broad range of smartphones, including iOS, Android, RIM, Symbian, and Windows Phone 7 handsets. The spying software has the capability to monitor and report back on calls and GPS positions from mobile phones, as well as recording Skype sessions on a PC, logging keystrokes, and controlling any cameras and microphones that are installed. [11]
- Egyptian dissidents who ransacked the office's of Egypt's secret police following the overthrow of Egyptian President Hosni Mubarak reported they discovered a contract with Gamma International for €287,000 for a license to run the FinFisher software. [12]
Malware
- Flame (malware)
- Flame related articles
- Flame, also known as Flamer, sKyWIper, and Skywiper, is modular computer malware discovered in 2012 that attacks computers running the Microsoft Windows operating system. The program is being used for targeted cyber espionage in Middle Eastern countries. Its discovery was announced on 28 May 2012 by MAHER Center of Iranian National Computer Emergency Response Team (CERT), Kaspersky Lab and CrySyS Lab of the Budapest University of Technology and Economics. The last of these stated in its report that it "is certainly the most sophisticated malware we encountered during our practice; arguably, it is the most complex malware ever found." Flame can spread to other systems over a local network (LAN) or via USB stick. It can record audio, screenshots, keyboard activity and network traffic.[6] The program also records Skype conversations and can turn infected computers into Bluetooth beacons which attempt to download contact information from nearby Bluetooth-enabled devices. This data, along with locally stored documents, is sent on to one of several command and control servers that are scattered around the world. The program then awaits further instructions from these servers. (wikipedia)
- Flame related articles
Operating Systems
- Backdoors
- Some of the information strikes me as outdated, as I am aware of at least one large nation/economy which has removed Microsoft from its government computer systems and in now Linux-based, using proprietary software. This switchover began in 2004/5. In other words, that country's government was aware of the "backdoor" in Microsoft which allowed the US to spy on them -- and they weren't having it anymore. [13]
Windows 8
- Windows 8 Will Have a “Kill Switch”
- The very anticipated operating system Windows 8 will have a feature that was never found on PC’s before: A kill switch that can remotely delete software and edit code without the user’s permission. Although Microsoft claims the switch would only be used for software that is downloaded from its app store, no official policies clearly define the actual purpose of the kill switch. In other words, nothing is truly considered “illegal” and that includes issues regarding spying, censorship and free speech. [14]
Video cameras
RFID systems
(todo)
- In passports, corporate service cards, consumer goods, ...
- Ex-IBM Employee reveals TV Abandoned Analog Band to Make Room for RFID Chips
- Hitachi Develops World's Smallest RFID Chip
- The Japanese giant Hitachi has developed the world's smallest and thinnest Radio Frequency Identification (RFID) chip. Measuring only 0.15 x 0.15 millimeters in size and 7.5 micrometers thick, the wireless chip is a smaller version of the previous record holder - Hitachi's 0.4 x 0.4 mm "Micro-Chip". The company used semiconductor miniaturization and electron beam technology to write data on the chip substrates to achieve this decrease in size. The new chips have a wide range of potential applications from military to transportation, logistics and even consumer electronics. According to the Nikkei website, Hitachi is now planning on developing an even smaller RFID chip using 65-nanometer lithographic technology.
Entertainment devices
- Digital TV's
- Online game consoles
- Players’ behaviour in the game is monitored by companies who aim to understand the new opportunities for emerging real-life markets. A whole new class of corporate game player has emerged. These players research the habits of people via their avatars and market both virtual and real products inside and outside these worlds to other players. p.77 - 36. Virtual Tracking
- XBox One: A device brought into your home with 4 microphones, 2 cameras, an infrared motion sensor, and a license to freely record and upload your activity… "to the maximum extent permitted by law, we may monitor your communications and may disclose information about [15]
- Players’ behaviour in the game is monitored by companies who aim to understand the new opportunities for emerging real-life markets. A whole new class of corporate game player has emerged. These players research the habits of people via their avatars and market both virtual and real products inside and outside these worlds to other players. p.77 - 36. Virtual Tracking
- Phone-home set-top boxes
Global
Interpol
(todo)
NATO
(todo)
Europe
European Union
- EU INDECT
- "UE FP7 INDECT Project: "Intelligent information system supporting observation, searching and detection for security of citizens in urban environment. Project Description: Intelligent information system supporting observation, searching and detection for security of citizens in urban environment.
- The main objectives of the INDECT project are:
- to develop a platform for: the registration and exchange of operational data, acquisition of multimedia content, intelligent processing of all information and automatic detection of threats and recognition of abnormal behaviour or violence,
- to develop the prototype of an integrated, network-centric system supporting the operational activities of police officers, providing techniques and tools for observation of various mobile objects,
- to develop a new type of search engine combining direct search of images and video based on watermarked contents, and the storage of metadata in the form of digital watermarks,[2].
- The main expected results of the INDECT project are:
- to realise a trial installation of the monitoring and surveillance system in various points of city agglomeration and demonstration of the prototype of the system with 15 node stations,
- implementation of a distributed computer system that is capable of acquisition, storage and effective sharing on demand of the data as well as intelligent processing,
- construction of a family of prototypes of devices used for mobile object tracking,
- construction of a search engine for fast detection of persons and documents based on watermarking technology and utilising comprehensive research on watermarking technology used for semantic search,
- construction of agents assigned to continuous and automatic monitoring of public resources such as: web sites, discussion forums, UseNet groups, file servers, p2p networks as well as individual computer systems,
- elaboration of Internet based intelligence gathering system, both active and passive, and demonstrating its efficiency in a measurable way.[3]
- INDECT partners:
- AGH Univeristy of Science and Technology (Poland) - Project Coordinator http://www.agh.edu.pl/en
- 2. Gdansk University of Technology (Poland) http://www.pg.gda.pl
- 3. InnoTec DATA G.m.b.H. & Co. KG (Germany) http://www.innotec-data.de
- 4. Grenoble INP (France) http://www.grenoble-inp.fr
- 5. MSWIA - General Headquarters of Police (Poland) http://www.policja.pl/
- 6. Moviquity (Spain) http://www.moviquity.com/webingles/index.htm
- 7. PSI Transcom GmbH (Germany) http://www.psi.de/
- 8. Police Service of Northern Ireland (United Kingdom) http://www.psni.police.uk/
- 9. Poznan University of Technology (Poland) http://www.put.poznan.pl
- 0. Universidad Carlos III de Madrid (Spain) http://www.uc3m.es
- 1. Technical University of Sofia (Bulgaria) http://www.tu-sofia.bg
- 12. University of Wuppertal (Germany) http://www.uni-wuppertal.de
- 13. University of York (Great Britain) http://www.york.ac.uk
- 14. Technical University of Ostrava (Czech Republic) http://www.vsb.cz
- 15. Technical University of Kosice (Slovakia) http://www.tuke.sk/tuke?set_language=en&cl=en
- 16. X-Art Pro Division G.m.b.H. (Austria) http://www.x-art.at
- 17. Fachhochschule Technikum Wien (Austria) http://www.technikum-wien.at[4]
United Kingdom
- British SIS (or MI6)
- British Council
- "Private sector language schools with whom the British Council compete complain about the state subsidized competition. While the language teaching makes a profit, the accounting is not transparent and if it were privatized, it is doubtful the it could be promoted in the way it is at present." (wikipedia)
- "For many Russians and, indeed for many people who are suspicious of British motives all over the world, the British Council is an ideal target, not just because it is a symbol of British culture and learning but because it is popularly supposed to be a front for espionage activities." - from: "Its widely assumed that the British Council is a wing of our secret services"
- "Private sector language schools with whom the British Council compete complain about the state subsidized competition. While the language teaching makes a profit, the accounting is not transparent and if it were privatized, it is doubtful the it could be promoted in the way it is at present." (wikipedia)
- MI5
- "MI5, which has a target of increasing its current 3,000 staff to 4,000 by 2011, also insisted that it wanted to improve relations with Muslim communities." [16]
Germany
Italy
- DIS ("Dipartimento delle Informazioni per la Sicurezza" - secret service)
Netherlands
France
- French intelligence constitutes of two major units: the DGSE("In 2009, the DGSE had an estimated staff of approximately 5,000 employees." [17]) the external agency and the DCRI the domestic agency. The latter being part of the police while the former is associated to the army. The DGSE is notorious for the Sinking of the Rainbow Warrior, but it is also known for revealing the most extensive technological spy network uncovered in Europe and the United States to date through the mole Vladimir Vetrov.
- Alexandre de Marenches head of the DGSE was a Knight of Malta. [18]
Spain
- CNI "Centro Nacional de Inteligencia" Employees +/- 2200. The National Intelligence Center (Spanish: Centro Nacional de Inteligencia, CNI) is the Spanish official intelligence agency. Its headquarters are located in the A-6 motorway near Madrid. The CNI is the successor of the Centro Superior de Información de la Defensa, Higher Centre for Defense Intelligence. Its main target areas are North Africa and South America and it operates in more than 80 countries. CNI's budget for 2010 is approximately 255 million euros. [19]
Romania
- CNSAS ("National Council for the Study of Securitate Archives") (Romania)
North America
United States
- See also:
- US secret service IP's: "Now, if you scan these IP addresses, you will find that they all match up...the list is somewhat outdated I suspect, but since they all match up (...) If you trace these IPs most will lead back to "The Internet Access Company" [??], and they also go through Cogent Communications, a Washington DC based tech company that has been doing quite well for being a very young business."
- Todo: Military forts (especially large-scale underground complexes - DUMBs)
Nuclear powered drilling machines? [2]
Patent (number 3,885,832) exist for such machine Subterrene [3]
NSA
“The technotronic era involves the gradual appearance of a more controlled society. Such a society would be dominated by an elite, unrestrained by traditional values. (...) The capacity to assert social and political control over the individual will vastly increase. It will soon be possible to assert almost continuous surveillance over every citizen and to maintain up-to-date, complete files, containing even most personal information about the health or personal behavior of the citizen in addition to more customary data. These files will be subject to instantaneous retrieval by the authorities.”-Zbigniew Brzezinski, protegé of David Rockefeller, cofounder of the Trilateral Commission, and NSA to Jimmy Carter, from his 1971 book Between Two Ages[20]
- William Binney, a former official with the National Security Agency, recently said that domestic surveillance in the U.S. has increased under President Obama, and trillions of phone calls, emails and other messages sent by U.S. citizens have been intercepted by the government. In fact, in an interview with Democracy Now, the official-turned-whistleblower claims that the government currently possesses copies of almost all emails sent and received in the United States. Binney, who is regarded as one of the best mathematicians and code breakers in NSA history, says he left the agency in late 2001 after he learned about its plan to use the September 11th terrorist attacks as an excuse to launch a controversial data collection program on its own citizens. One commercial company he claims to have participated in the program is AT&T, which he says handed over more than 320 million records of citizen-to-citizen communications that took place within the U.S. The program, which Binney says he helped create, was never meant for domestic surveillance but the agency has supposedly been spying on U.S. citizens for more than a decade now. According to Binney, once the software intercepts a transmission it will then build profiles on every person referenced in the data. The NSA is now in the process of building a $2 billion data storage facility in Utah that is bigger than anything Google (GOOG) or Apple (AAPL) has ever built, and Binney calculates that the facility will be able to store 100 years worth of the world’s electronic communications. [21]
- The NSA is building an enormous spy center, probably the biggest ever, in Bluffdale Utah. When construction is completed in 2013, the heavily fortified $2 billion facility will encompass 1 million square feet, including four 25,000-square-foot areas to house endless rows of high-powered servers. The center will be fed data collected by the agency’s eavesdropping satellites, overseas listening posts, and secret monitoring rooms in telecom facilities throughout the US. [22]
- The NSA Is Building the Country’s Biggest Spy Center
- NSA whistle blowers warn that the US government can use surveillance to ‘see into your life’
- The National Security Agency (NSA) headquarters in Fort Meade, Maryland. Among other forms of intelligence-gathering, the NSA secretly collects the phone records of millions of Americans, using data provided by telecom firms AT&T, Verizon and BellSouth. "Every day, collection systems at the National Security Agency intercept and store 1.7 billion e-mails, phone calls and other types of communications. And the Obama administration has formally demanded that it have access to any and all forms of internet communication."[23]
- The NSA is building an enormous spy center, probably the biggest ever, in Bluffdale Utah. When construction is completed in 2013, the heavily fortified $2 billion facility will encompass 1 million square feet, including four 25,000-square-foot areas to house endless rows of high-powered servers. The center will be fed data collected by the agency’s eavesdropping satellites, overseas listening posts, and secret monitoring rooms in telecom facilities throughout the US. [22]
- See also:
CIA
- Reinhard Gehlen also had profound influence in helping to create the National Security Council, from which the National Security Act of 1947 was derived. This particular piece of legislation was implemented to protect an unconscionable number of illegal government activities, including clandestine mind control programs. [24]
- The CIA was founded by William Donovan, a Knight of Malta who had been awarded the highest award in the Roman Catholic Church. The first director of the CIA, Allen Dulles, was a Knight of Malta whose nephew, Avery Dulles, was a prominent Jesuit priest. CIA directors William Colby, William J. Casey, John McCone, Allen Dulles, George Tenet, and Leon Panetta have all been either Knights of Malta or Jesuit-trained. [25]
- National Intelligence Council is small think tank of senior analysts reporting to the Director of Central Intelligence that produces estimates on priority national security issues for the President and his top advisers. [26] by John C. Gannon
- The 1997 CIA budget was 26.6 billion dollars. This year (1998) their budget is $26.7 billion [27]
- HUD’s Missing Money, Catherine Fitts, Hamilton Securities and the CIA.
- The fraudulent movement of finances through HUD were made possible by poor auditing standards that enabled as much as tens of billions of dollars to go annually missing. In a March 2000 report, the HUD (fraud scandal) Inspector General, Susan Gaffney, reported a high number of ‘adjustments’ that had to be made to account for $59 billion that could not be located in 1999 [28]
- video: US Foreign Policy - Secret Wars of the CIA
- Profile: Central Intelligence Agency (CIA) (historycommons.org)
- CIA Plans to Shift Work to Denver
FBI
- The FBI was founded by Charles J. Bonaparte (a grandson of Jérôme Bonaparte, the youngest brother of the French Emperor Napoleon I), a Knight of Malta who served on the board of trustees for the Catholic University of America. FBI directors Louis Freeh and Thomas Pickard are devoutly Roman Catholic and Louis Freeh is an alleged member of Opus Dei. [29]
- See also:
- COINTELPRO
- The COINTELPRO Papers
- COINTELPRO Article at http://decryptedmatrix.com [30] [31] [32] [33] [34]
DHS
- Department of Homeland Security (DHS) is a Jesuit operation. The first director was Tom Ridge, a devoutly Roman Catholic Knight of Columbus. The real power behind the DHS was John C. Gannon, the head of it's intelligence unit. Gannon was Jesuit-trained at the College of the Holy Cross and is a member of the Jesuit Volunteer Corps. The deputy director of the DHS from 2005-2007 was Michael P. Jackson, who was Jesuit-trained at Georgetown University. Bush's first pick for the second DHS director was a Roman Catholic man. In the end, he chose Michael Chertoff, who is married to a Jesuit professor (Meryl Chertoff). Under Chertoff, the head of the DHS' immigration was Emilio T. Gonzalez, a Knight of Malta. The new DHS director (Under Obama) is Janet Napolitano, who was Jesuit-trained at Santa Clara University. [35]
Other
- Information Awareness Office - Information-mining technology and mass surveillance system
- DEA
- tolink: ODNI, NIC, NNSA, DOJ, ATF, FINCEN, PFIAB, IOSS, NICX, the U.S. Marshals, Customs, the USPS Postal Inspectors, the Secret Service, Treasury, SBU (Ukraine), ASIS, NZSIS, BND, CSIC, CNI, NBH, ABW, SEID, SISD, the FSB, PRC Intelligence, ROC MJIB, the Japanese Naicho, and all of the U.S., SEATO and ASEAN Defense Departments.
- "Except for the CIA, intelligence offices or agencies are components of cabinet departments with other roles and missions. The intelligence offices/agencies, however, participate in Intelligence Community activities and serve to support the other efforts of their departments." ... "Intelligence Community. The Intelligence Community (defined at 50 U.S.C. 401a(4)) consists of the following:" (from "Intelligence Issues for Congress")
- National Security Agency (NSA)
- National Reconnaissance Office (NRO)
- Central Intelligence Agency (CIA)
- Bureau of Intelligence and Research (INR)
- National Geospatial-Intelligence Agency (NGA)
- Federal Bureau of Investigation (FBI)
- Defense Intelligence Agency (DIA)
- Army Intelligence
- Office of Naval Intelligence
- Air Force Intelligence
- Marine Corps Intelligence
- Coast Guard (CG)
- Treasury Department
- Energy Department
- Drug Enforcement Agency (DEA)
- National Health Intelligence Network (NHIN)
- Bureau of Firearms/xplosives, Tobacco and Alcohol (BFTA)
Canada
- CSIS (Canada)
Israel
Russia
- GRU (1918, created by Jesuit coadjutor Lenin)
- FSB (Russia)
- Foreign Intelligence Service (Russia)
- "KGB's archives affords me a glimpse at Vatican's Intelligence Service":
- "Stanislav Lekarev, a well-placed investigative reporter and a former Soviet official, reveals the results of his heart-to-heart with a friend that still has access to the documents from KGB's 5th Chief Directorate that was also responsible for dealing with religious dissent. Despite the Holy See's curt, Jesuit-like denial of having any involvement in intelligence activities, the archives shed rare light on the Vatican's well-though-thinly-cloaked clandestine activities in USSR. Vatican's Secret Service is a well-compartmentalized into its many cover organizations conveniently subdivided by their religious activities that afford the Holy See the advantages over any other intelligence service. The strategically important service is the responsibility of the Jesuits. The order is under the direct command of the pontiff. The Jesuits manage information-gathering functions for the Vatican. Thus the Russian department is conveniently set up under the cover of the Congregation of the Eastern Churches, Actione Catolica, Russia Christiana, and has its operations center at the St. Georgio Institute in Medona, and at the Modesto Monastery in Seriate, a picturesque suburb of Milan. The department that runs its agents in Russia is the mysterious Russicum [36], which has a legitimate appearance of any other Catholic outreach facility, recruiting into its ranks residents of Eastern Europe. Information gathering takes place under the guise of very conventional missionary activity, a non-governmental charity work, seemingly innocent purchase of a government's archives. The Russian desk is still run by its Vatican's former USSR directorate which bears the name of the St. Teresa Russian Catholic College. The external and hands-on operations are also performed by the Dominican Order. The order uses its international resources to exfiltrate its agents, to discredit undesirable officials, and other cloak and dagger operations. Its low-profile department of Sodalicium Pianium is responsible for internal security, taking care of the Vatican's own heretics, and vetting out Vatican's security apparatus. Thus Vatican has plenty of organizations to also collaborate with other intelligence agencies. Joint projects with CIA, MI6, SDECE and Mossad has been through The Sovereign Military and Hospitaller Order of St. John of Jerusalem of Rhodes and of Malta. Pinochet and the Polish Solidarnosc (Solidarity) are good examples of Vatican's intelligence networking par excellence."
- "Vatican intelligence has spied on Russia for many years"
- [Russia’s Security Service Could Gain Powers Formerly Associated With Soviet KGB]
- Russia’s parliament is considering a new law that would extend the powers of the country’s secret security agency, the FSB. If the bill is passed, it would restore practices once associated with the infamous KGB. Russia’s security services have steadily regained power and influence under Prime Minister Vladimir Putin, himself a former KGB officer. Human rights advocates are concerned that the new measures could further curtail the rights of government critics and the independent media.
- "KGB's archives affords me a glimpse at Vatican's Intelligence Service":
Asia
China
- ...
- Companies
Pakistan
- ISI
- Many in the Pakistani government, including slain former Prime Minister Benazir Bhutto, have called the intelligence agency "a state within a state," working beyond the government's control and pursuing its own foreign policy. [37]
Literature
 [38] The CIA and the cult of intelligence, Victor Marchetti, ISBN 978-0440203360
[38] The CIA and the cult of intelligence, Victor Marchetti, ISBN 978-0440203360
 Blank Check: The Pentagon's Black Budget, Tim Weiner, ISBN 978-0446392754
Blank Check: The Pentagon's Black Budget, Tim Weiner, ISBN 978-0446392754